Cyber security awareness: COVID-19 exploited by malicious cyber actors
The highlights of the advisory are:
Malicious groups are using the COVID-19 pandemic as part of their cyber operations. These cyber threat actors will often masquerade as trusted entities. Their activity includes using coronavirus-themed phishing messages or malicious applications, often masquerading as trusted entities that may have been previously compromised.
Cyber criminals are using the pandemic for commercial gain, deploying a variety of ransomware and other malware. They are likely to continue to exploit the COVID-19 pandemic over the coming weeks and months. Threats observed include:
-
Phishing, using the subject of coronavirus or COVID-19 as a lure;
-
Malware distribution, using coronavirus or COVID-19-themed lures; and
-
Registration of new domain names containing wording related to coronavirus or COVID-19.
Malicious cyber actors rely on basic social engineering methods to entice a user to carry out a specific action. These actors are taking advantage of human traits such as curiosity and concern around the coronavirus pandemic in order to persuade potential victims to:
-
Click on a link or download an app that may lead to a phishing website, or the downloading of malware, including ransomware. For example, a malicious Android app purports to provide a real-time coronavirus outbreak tracker but instead attempts to trick the user into providing administrative access to install 'CovidLock' ransomware on their device.
-
Open a file (such as an email attachment) that contains malware. For example, email subject lines contain COVID-19 related phases such as 'Coronavirus update' or '2019-nCov: Coronavirus outbreak in your city (Emergency)'.
To create the impression of authenticity, malicious cyber actors may spoof sender information in an email to make it appear to come from a trustworthy source, such as the World Health Organisation (WHO) or an individual with 'Dr.' in their title. In several examples, actors send phishing emails that contain links to a fake email login page. Other emails purport to be from an organisation's human resources (HR) department and advise the employee to open the attachment.
Malicious file attachments containing malware payloads may be named with coronavirus or COVID-19-related themes, such as 'Prime Minister discusses budget savings due to coronavirus with Cabinet.rtf'.
The National Cyber Security Centre have observed a large volume of phishing campaigns that use the social engineering techniques described above.
Examples of phishing email subject lines include:
-
2020 Coronavirus Updates;
-
Coronavirus Updates;
-
2019-nCov: New confirmed cases in your City; and
-
2019-nCov: Coronavirus outbreak in your city (Emergency).
These emails contain a call to action, encouraging the victim to visit a website that malicious cyber actors use for stealing valuable data, such as usernames and passwords, credit card information, and other personal information.
Most phishing attempts come by email but NCSC has observed some attempts to carry out phishing by other means, including text messages (SMS).
Historically, SMS phishing has often used financial incentives – including government payments and rebates (such as a tax rebate) – as part of the lure. Coronavirus-related phishing continues this financial theme, particularly in light of the economic impact of the pandemic and the governments' employment and financial support packages. For example, a series of SMS messages uses a UK government-themed lure to harvest email, address, name, and banking information. These SMS messages – purporting to be from 'COVID' and 'UKGOV' (see figure 1) – include a link directly to the phishing site (see figure 2).
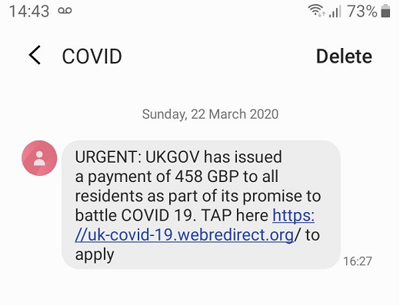
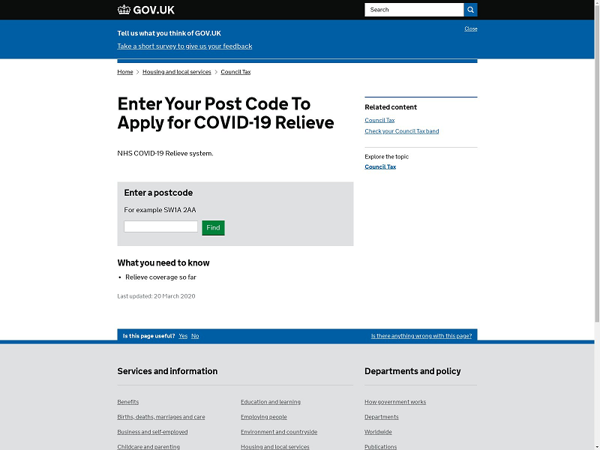
Figure 2: UK government-themed phishing page
As this example demonstrates, malicious messages can arrive by methods other than email. In addition to SMS, possible channels include WhatsApp and other messaging services. Malicious cyber actors are likely to continue using financial themes in their phishing campaigns. Specifically, it is likely that they will use new government aid packages responding to COVID-19 as themes in phishing campaigns.
A number of actors have used COVID-19-related phishing to steal user credentials. These emails include previously mentioned COVID-19 social engineering techniques, sometimes complemented with urgent language to enhance the lure. If the user clicks on the hyperlink, a spoofed login webpage appears that includes a password entry form. These spoofed login pages may relate to a wide array of online services including – but not limited to – email services provided by Google or Microsoft, or services accessed via government websites.
The NCSC's top tips for spotting a phishing email are:
- Authority – Is the sender claiming to be from someone official (e.g. your bank or doctor, a lawyer, a government agency)? Criminals often pretend to be important people or organisations to trick you into doing what they want.
- Urgency – Are you told you have a limited time to respond (e.g. in 24 hours or immediately)? Criminals often threaten you with fines or other negative consequences.
- Emotion – Does the message make you panic, fearful, hopeful. or curious? Criminals often use threatening language, make false claims of support, or attempt to tease you into wanting to find out more.
- Scarcity – Is the message offering something in short supply (e.g. concert tickets, money, or a cure for medical conditions)? Fear of missing out on a good deal or opportunity can make you respond quickly.
Please continue to be extra vigilant during this unprecedented time and please do not click on any links in unexpected emails, texts, or other messages.
If you wish to read the full advisory it can be found here: ncsc.gov.uk/news/covid-19-exploited-by-cyber-actors-advisory
